
Each year, thousands of UK businesses fall victim to cyber attacks. From Phishing scams to ransomware, the threats are multiplying, with attackers...
Read more
Picture this: Your business gets hit by a ransomware attack, and your valuable data is locked away by cyber criminals demanding a huge ransom...
Read more
Don’t think your business is a target? Think again You might think that cyber criminals are only interested in large companies or those with...
Read more
Breached or stolen passwords are the bane of any organization’s cybersecurity. Passwords cause over 80% of data breaches. Hackers get in using...
Read more
In the pulsating digital landscape, every click and keystroke echoes through cyberspace. The battle for data security rages on. Businesses stand as...
Read more
Imagine you’re working away on your PC and see a Windows update prompt. Instead of ignoring it, you take action. After all, you want to keep your...
Read more
Smart homes have become a ubiquitous part of modern living. It doesn’t even seem unusual anymore to tell your refrigerator to add milk to the...
Read more
Software-as-a-Service (SaaS) has revolutionized the way businesses operate. It offers convenience, scalability, and efficiency. No more dragging...
Read more
Did you know that a staggering 60% of phishing websites are only online for a fleeting 10 minutes? Yes, you read that right. Just ten...
Read more
We’ve all been there. You’re scrolling through your Facebook feed, and an ad pops up promising to help you grow your business with some...
Read more
You may think that cyber attacks only happen to large corporations. But unfortunately, that’s not the case. According to a recent report,...
Read more
Have you heard the saying, “A picture is worth a thousand words”? It seems cyber criminals have too, and they’re using it to their...
Read more
Don’t be mistaken, we love Microsoft Edge (and think you will too), but lately, something has come to our attention that we wanted to...
Read more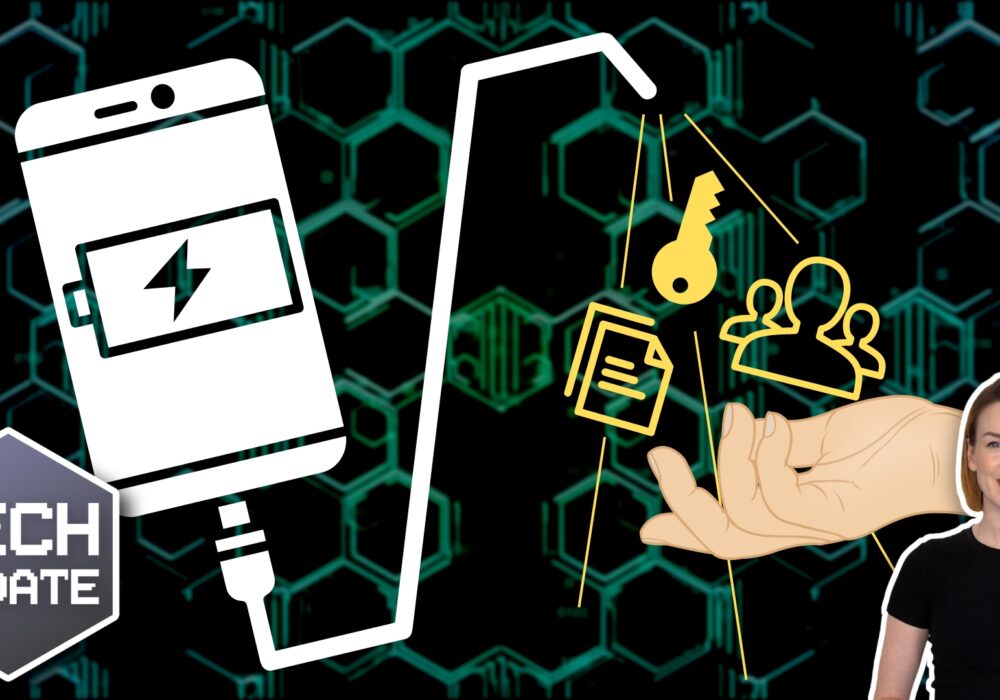
Airports, hotels, cafés, even shopping centres, offer public charging points where you can boost your phone or laptop battery on the...
Read more
The second of the five controls we are going to explore is Secure Configuration. This involves making device and software settings as secure as...
Read moreWe won’t fill your inbox with spam – but we will send out a short newsletter once a month (or less) with news and updates.
Whether you need IT support for small businesses or a school, we’re here to help.