Cyber crime is one of the leading threats facing UK businesses. Cyber criminals are becoming more sophisticated and organised, launching attacks on an unprecedented scale, with many of these targeting smaller businesses that lack the cyber security infrastructure necessary to defend themselves. Here are some of the statistics that illustrate the scale of the problems businesses face:
- According to the UK Government’s Cyber Breaches Survey 2023, an estimated 39 million instances of cyber crime were perpetrated against businesses in the last 12 months.
- The average cost of a materially impactful cyber incident is estimated at £15,300 per victim.
- Phishing scams are the most common form of cyber crime, both in the UK, and globally. A 2023 report by Verizon found phishing to be a factor in 36% of all data breaches.
- The UK is believed to be Europe’s biggest target for phishing attacks, with 96% of UK organisations targeted in 2022.
- Ransomware attacks are increasing in frequency and severity, accounting for 34% of UK cyber breach incidents in 2022 according to data from the ICO.
In today’s hostile cyber crime landscape, adopting a passive approach to threat management simply isn’t an option. Cyber breaches can have a severe impact on a business’s financial stability, with regulatory penalties, ransom payments, operational disruption, and possible legal action combining to impose a heavy financial burden on those affected. Attacks can also result in serious reputational damage, which can subsequently impact sales and growth well beyond the incident itself.
BCNS – IT Support and Strategic Solutions for Devon Businesses
BCNS provides IT services and solutions to businesses across Devon, helping them to operate productively and securely using transformative technologies. Over the past decade, a strong cyber security posture has become a strategic necessity for any business. Cyber criminals will exploit any loophole they can find to steal valuable information, commit acts of fraud, and hold businesses to ransom, with attacks becoming more frequent and damaging.
This short blog series provides a checklist of the cyber security controls you can use to reinforce your digital assets against cyber threats and data loss. In this article, we’ll focus on the organisational steps, including both policies and practices, you should consider to achieve a robust security posture. Here are 4 policies and best practices for cyber safety in 2024.
Secure Password Practices
Many cyber breaches leverage weak account credentials as an entry point, with criminals able to hack weak passwords using a combination of technical tools and guesswork. Effective password management is therefore a vital cyber security safeguard, helping to protect sensitive information against unauthorised access and cyber threats. Here are some best practices you should deploy to guard accounts against hacking attempts:
Create Strong Passwords: Urge employees to create long, complex, and unique passwords for each account. Promote a mix of upper- and lower-case letters, as well as numbers and special characters. In the past, changing passwords regularly was a recommended practice. Today, however, experts agree that strength and complexity should be prioritised over frequent changes, and that passwords should only be changed when there is reason to believe an account has been compromised.
Create and Enforce Password Policies: Create password policies that specify minimum criteria all passwords must meet in terms of length and complexity. Enforce these policies using technical controls, and activate account lockout features to protect against brute force hacking attempts.
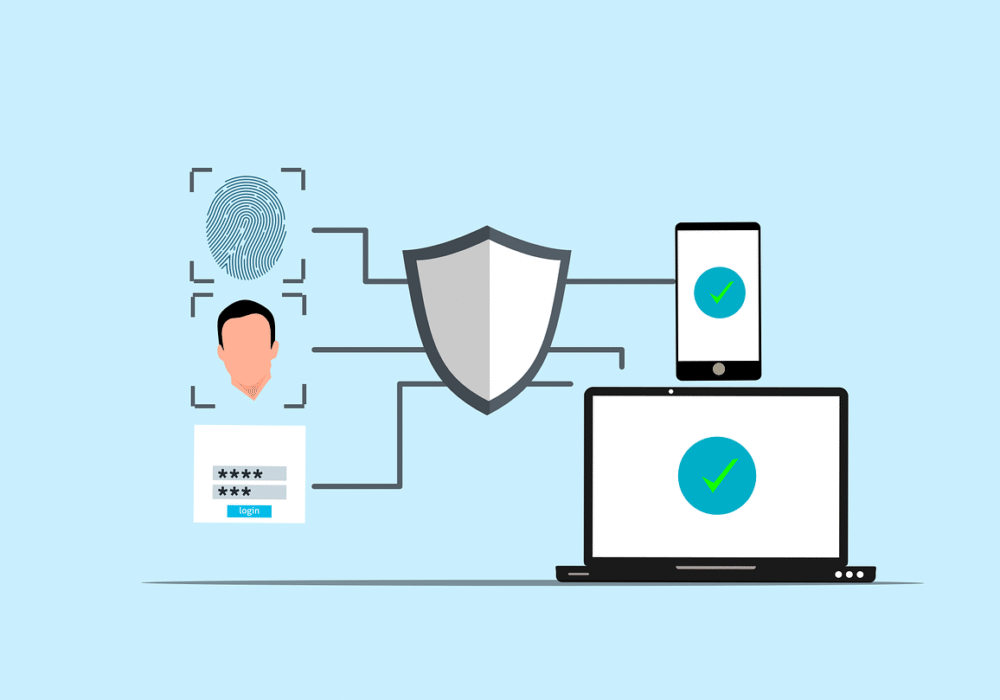
Use Multi-factor Authentication: Supplement strong passwords with multi-factor authentication, a secure authentication protocol that requires users to submit an additional form of ID verification when logging into an account. This additional identifier could include a biometric attribute such as a fingerprint scan, a one-time passcode sent to a registered secondary device, or a security token.
Information Security Policies
Information security policies are documents that provide detailed guidance on securely managing, protecting, and interacting with a company’s digital systems. The guiding objective of these documents is to ensure the ongoing confidentiality, integrity, and availability of information assets. Policies should be broad in scope, covering all security domains and business activities that involve sensitive data, including (but not limited to) the following:
Access Controls: This policy should define how access rights and user privileges are applied and managed. In the interests of risk mitigation, employees should only have access to systems and data necessary for them to perform their job roles – a concept known as ‘the principle of least privilege.’
Acceptable Use: An acceptable use policy should contain actionable rules and best practices for employees to follow when interacting with digital systems and sensitive information. It should set clear boundaries on the use of personal devices for work purposes, provide guidelines for secure remote access, and set out incident reporting procedures. It should also emphasise any actions and behaviours that are prohibited, such as sharing company information on social media, or downloading software without permission.
Data Encryption: This policy should contain rules and guidelines on the application of encryption. Encryption should be used tactically to protect critical information against unauthorised access, both in transit and at rest.
Data Loss Prevention: A data loss prevention policy should outline the strategies, tools, and procedures required to protect sensitive information against unpermitted access, theft, corruption, or deletion. It should define rules for data classification, specify how access should be granted and managed, and set out procedures for responding to data loss incidents.
These are just some of the subject matter areas information security policies should cover. If in doubt, seek the support of your IT support provider. They should be able to guide you in establishing policies that are appropriate for your business.
Business Continuity and Disaster Recovery Planning
A Business Continuity and Disaster Recovery plan (often shortened to ‘BCDR’), is a strategic document that should aim to help your business recover quickly following various setbacks, including IT outages, cyber attacks, data breaches and natural disasters.
A BCDR strategy should be informed by a comprehensive risk assessment exercise and a Business Impact Analysis (BIA). This will ensure that BCDR measures prioritise the data and systems most at risk, and most critical to business operations.
An effective BCDR strategy should contain the following elements:
Data Backup Instructions: The strategy should contain clear guidance on the use of data backup systems. Step-by-step instructions should be provided, and those tasked with implementing the backup process should be named.
Recovery Procedures: Provisions should also be made that allow a complete and swift recovery of vital digital infrastructure, including servers, networks, and applications. Again, clear, methodical instructions should be provided, detailing the redundancies and failovers to be actioned.
Security Awareness Training
Modern cyber threats are escalating rapidly, with criminals developing new techniques and exploits all the time. Despite this, human error and negligence remains a leading cause of data breaches, with as many as 95% of security incidents attributable to some form of human error.
By enrolling your employees on a comprehensive security awareness training programme, you can equip your team with the skills they need to defeat common cyber threats and operate securely and compliantly. When implementing awareness training, make sure it’s mandatory for staff at all levels of your business, and ensure the learning material covers a wide range of topics. Consider the following:
Phishing
Educate staff on the dangers of phishing, including the techniques employed, the impact phishing scams can have, and the characteristics common to these attacks, so that employees know what to look out for. Consider using training resources that combine flexible online learning modules with phishing simulation exercises.
Password security
Awareness training should promote password security best practices. Highlight the dangers of weak account passwords, and explain the methods and tools attackers use to crack into poorly defended accounts. Promote the use of long, complex, and unique passwords, encourage the use of a password manager (if this is a company policy), and stress the importance of using multi-factor authentication.
Secure Browsing and Email Management
Ensure staff understand the threats they can encounter when handling emails and browsing the internet. Promote a range of best practices, including:
- Checking for a secure connection when visiting a new website.
- Inspecting email headers – to ensure an email originates from its claimed source.
- Exercising caution when clicking through links or downloading email attachments from unknown sources.
- Avoiding the use of public Wi-Fi networks where possible.
Data Protection and Privacy
Inform staff of their responsibilities in terms of handling sensitive information securely. Ensure staff are able to identify protected categories of information, and the elevated privacy and security protections that apply to these data types. Set clear, unequivocal boundaries on the safe transmission and storage of data, ensuring staff are aware of practices that are strictly prohibited – such as storing and sharing businesses data on personal devices that aren’t under the control of your business.
In Summary
Establishing a solid cyber security framework can seem daunting, but with a systematic and methodical approach, you can establish the practices and policies you need to keep the majority of cyber threats at bay. Coming up next, we’ll explore 4 technical protections all businesses should use to protect their digital assets.
BCNS – Security-focused IT services for Devon Businesses
From IT support and infrastructure, to cloud and connectivity solutions, BCNS is a full-service IT provider committed to helping Devon’s businesses gain a strategic advantage through the power of technology. Today’s hostile threat environment requires potent defences. Our managed cyber security services offer a full complement of protections, covering everything from your network perimeter to your email accounts. We apply advanced, real-time threat monitoring to identify and neutralise security risks before they have a chance to impact your systems.
Keen to know more? Get in touch with BCNS today, and we’ll help you address your business’s cyber security challenges.