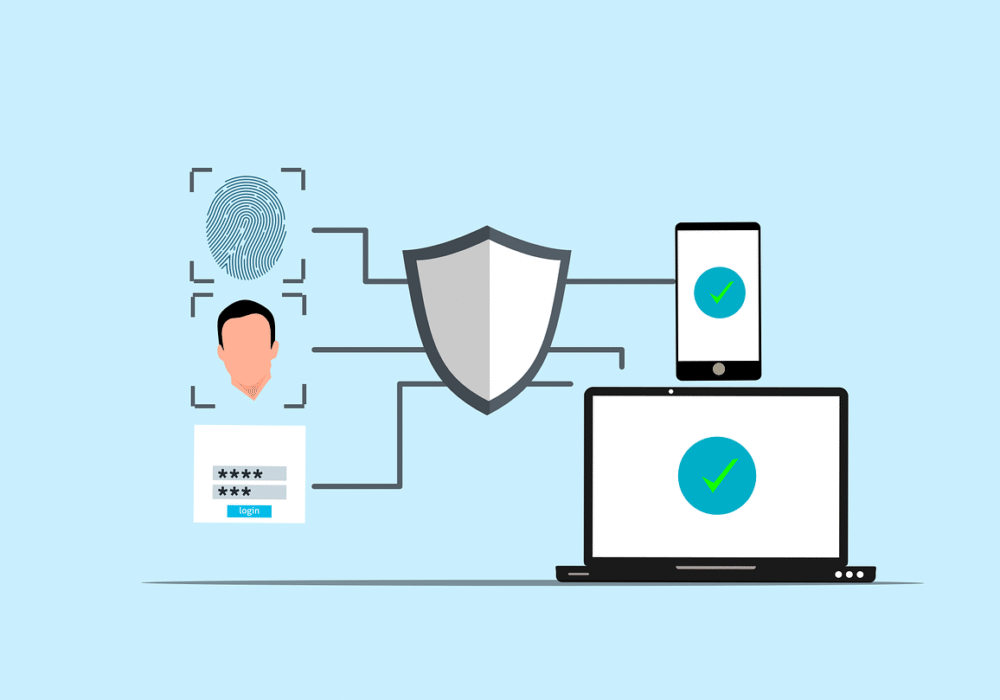
Having Access Controls will ensure that user accounts can only access the networks, computers, and applications that that user needs to perform their role to the best of their ability. ‘Need’ is an important word here – the Cyber Essentials Accreditation requires that user accounts are only assigned to authorised individuals and not just anybody.
Access controls are an effective way to ensure your business is secure. The way we have been forced to work recently, with a lot of us going remote, has highlighted just how important Access Controls are.
Access Controls – The requirements outlined by Cyber Essentials
You must control access to data. There must be controls on what changes can be made to administrative accounts, and the privileges around access to those accounts should only be given when absolutely necessary to those that need them.
The user accounts in your business allow the use of all applications and devices, they are also your direct access to all of your clients’ sensitive information. By only permitting access to authorised personnel to accounts that mirror their role in the organisation you will massively reduce the risk of your information being damaged or stolen.
The consequences of an account with privileged access to devices, applications, and information being breached could be disastrous. They could even be used to facilitate a large-scale attack at a later date, causing even more damage – operationally, financially, and reputationally.
Let’s have a look at a real-world example.
Administrative accounts
For example:
James is logged onto an administrative account and is going about his normal workday when he receives and opens a malicious email attachment. Using the access privileges that James has, the Malware virus Ransomware successfully encrypts all the data on the company network, demanding a ransom for the safe return of access and control.
You may not think this applies to you, but, in actual fact, small to medium businesses are more likely to be the victim of such an attack, and Ransomware attack frequency is at an all-time high.
Requirements for Cyber Essentials Accreditation
1. You must have full control over all accounts and the access privileges to each of them.
2. You must have a user account creation and approval process in place within the organisation.
3. Users must be authenticated before granting access to application devices, and all credentials for each must be entirely unique.
4. You must disable all user accounts as soon as they are no longer in use. Special access privileges to individual accounts must also be restricted when no longer needed – for example, when a team member changes departments, they no longer need access to their previous department’s account. It is recommended to implement two or multi-factor authentication to be sure that everyone has access only to information which is relevant to them.
Value from your tools
BCNS makes business easier and more cost-effective by guaranteeing that you and your team are always connected to each other and your clients. We can also guarantee that your team are using the latest version of every application to ensure that your systems are secure, and you are getting the best possible benefits from your tech. Our team of experts will assist you throughout the transition and beyond to be sure you achieve exactly what you desire. At the same time we can reduce your expenses and improve your security as well as performance! Contact us now and find out how we can help you with your business communications and move into a more productive future.